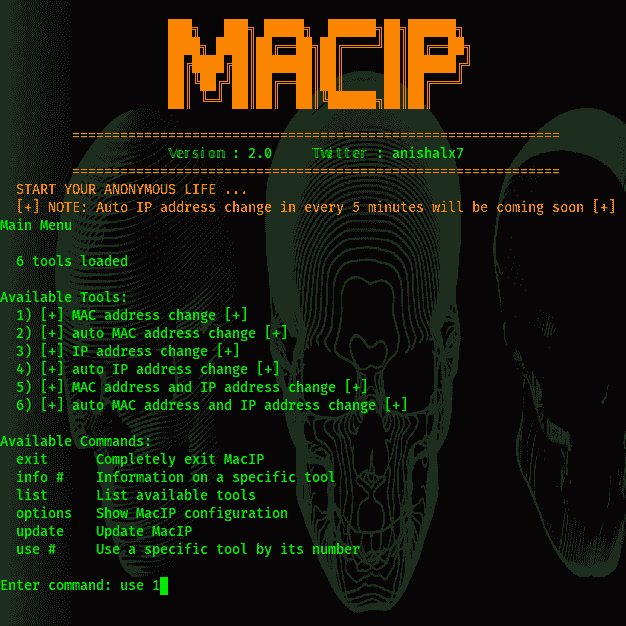
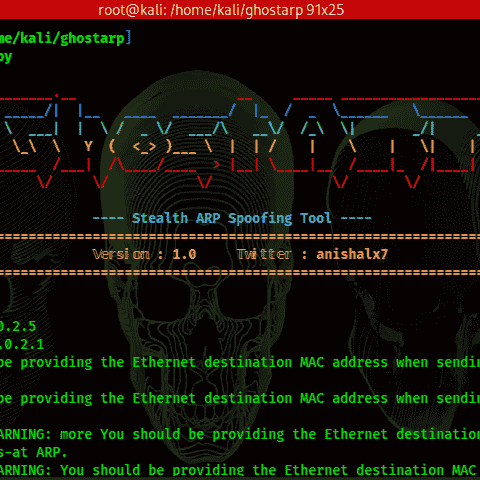
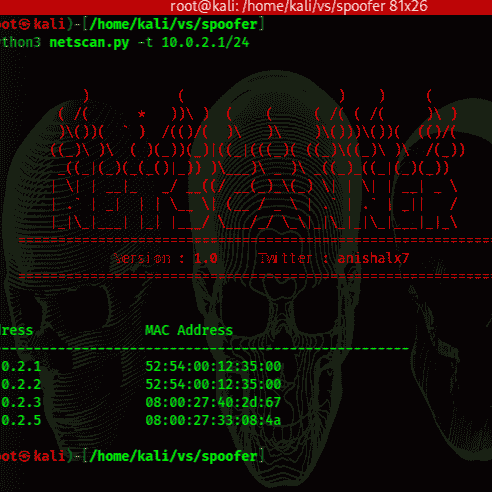
Anish Kumar
Making
good
code
since
2024
About me
What i do
Fixer
Solving daily technical problems enhances my skills for future challenges
Fixer
Solving daily technical problems enhances my skills for future challenges
Visual
I search the internet for references and then combine them to create my own work.
Visual
I search the internet for references and then combine them to create my own work.
Hunter
I'm passionate about bug bounty hunting, using various tools and my unique approach to find vulnerabilities
Hunter
I'm passionate about bug bounty hunting, using various tools and my unique approach to find vulnerabilities
Learner
I'm constantly learning to upskill my knowledge, utilizing free time for technical work and expanding my expertise in cybersecurity.
Learner
I'm constantly learning to upskill my knowledge, utilizing free time for technical work and expanding my expertise in cybersecurity.
Tutorial
I thought I’d make millions of $ from Youtube but I didn’t
Tutorial
I thought I’d make millions of $ from Youtube but I didn’t


Experience
Languages
Developed multiple Python tools
Experienced
Networking Automation Tools
Experienced
Utilized Bash for scripting
Intermediate
Scripting Task Automation
Intermediate
Built mini projects
Basic
System-Level Programming
Basic
Creating payloads with JavaScript
Basic
Payload Creation Scripts
Basic
Tools
Nmap
Nmap
Utilized Nmap for comprehensive network and domain scanning, mastering essential commands during my Z Security course.
Burp Suite
Burp Suite
Daily utilize Burp Suite to uncover website vulnerabilities, solve labs, and engage in bug bounty programs.
Metasploit
Metasploit
Mastered Metasploit and its commands for monitoring target machines during my Z Security courses.
Wireshark
Wireshark
Learned Wireshark to analyze and sniff target networks by creating my own lab for man-in-the-middle attacks.
kali linux
kali linux
Utilizing Kali Linux daily as my primary OS, I've conducted pentesting and mastered numerous tools and commands.
Maltego
Maltego
Learned Maltego during my Z Security course to gather OSINT and information about targets effectively.
Connect
Hiding
bad
code
since
2022
About me
What i do
Fixer
Solving daily technical problems enhances my skills
for
future challenges
Fixer
Solving daily technical problems enhances my skills
for
future challenges
Visual
I search the internet for references and then combine them to create my own work.
Visual
I search the internet for references and then combine them to create my own work.
Hunter
I'm passionate about bug bounty hunting, using various tools and my unique approach to find vulnerabilities
Hunter
I'm passionate about bug bounty hunting, using various tools and my unique approach to find vulnerabilities
Learner
I'm constantly learning to upskill my knowledge, utilizing free time for technical work and expanding my expertise in cybersecurity.
Learner
I'm constantly learning to upskill my knowledge, utilizing free time for technical work and expanding my expertise in cybersecurity.
Tutorial
I thought I’d make millions of $ from Youtube
but I
didn’t
Tutorial
I thought I’d make millions of $ from Youtube
but I
didn’t
Experience
Languages
Networking Automation Tools
Experienced
Networking Automation Tools
Experienced
Scripting Task Automation
Intermediate
Scripting Task Automation
Intermediate
System-Level Programming
Basic
System-Level Programming
Basic
Payload Creation Scripts
Basic
Payload Creation Scripts
Basic
Tools
Nmap
Utilized Nmap for comprehensive network and domain scanning, mastering essential commands during my Z Security course.
Nmap
Utilized Nmap for comprehensive network and domain scanning, mastering essential commands during my Z Security course.
Burp Suite
Daily utilize Burp Suite to uncover website vulnerabilities, solve labs, and engage in bug bounty programs.
Burp Suite
Daily utilize Burp Suite to uncover website vulnerabilities, solve labs, and engage in bug bounty programs.
Metasploit
Mastered Metasploit and its commands for monitoring target machines during my Z Security courses.
Metasploit
Mastered Metasploit and its commands for monitoring target machines during my Z Security courses.
Wireshark
Learned Wireshark to analyze and sniff target networks by creating my own lab for man-in-the-middle attacks.
Wireshark
Learned Wireshark to analyze and sniff target networks by creating my own lab for man-in-the-middle attacks.
kali linux
Utilizing Kali Linux daily as my primary OS, I've conducted pentesting and mastered numerous tools and commands.
kali linux
Utilizing Kali Linux daily as my primary OS, I've conducted pentesting and mastered numerous tools and commands.
Maltego
Learned Maltego during my Z Security course to gather OSINT and information about targets effectively.
Maltego
Learned Maltego during my Z Security course to gather OSINT and information about targets effectively.
My Projects
Connect